Ensuring secure communication in the future with quantum cryptography
In the future, our data will have to be even more secure than it is now. This will require new technologies, one of which is quantum cryptography. What is it? And how do we tackle the issue? Find out here in an interview with our researcher Iyán Méndez Veiga. Watch our new explanatory video.
Researchers around the world are working to bring quantum cryptography from theory to practice. The Applied Cyber Security Research Lab at the Lucerne School of Computer Science and Information Technology (HSLU) is also involved. In this interview, our expert and researcher Iyán Méndez Veiga explains the progress made and challenges associated with quantum cryptography. He talks about current projects at the Lucerne University of Applied Sciences and Arts and what drives him.
Iyán Méndez Veiga, for most people, the principle of quantum cryptography is difficult to understand. Is there a more familiar, everyday concept you can use to explain quantum cryptography?
Yes, think of it as a sealed letter: you put your secret key or password in an envelope and seal it. If someone tries to open the envelope, they break the seal and you will be able to see that it has been tampered with.
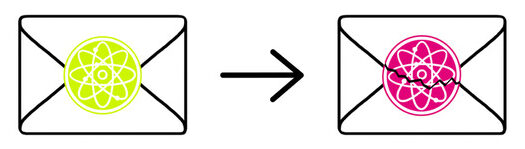
What happens in quantum cryptography is something similar. If you want to agree on a secret key with someone, you exchange photons. They are the particles of light and can be prepared in different states. If someone intercepts some of these photons and observes them, there is a good chance their state will change, which allows you to detect attackers eavesdropping on your secret. This property of quantum physics ensures the security of quantum cryptography.
Conventional encryption methods are only secure as long as the underlying mathematical problems are difficult to solve, but more advanced technologies such as quantum computers will have the capacity to solve some of these problems and, therefore, break the encryption techniques that rely on them.
Classical physics is fundamentally different from quantum mechanics in that looking at things does not change them. But imagine a situation where you cause a letter to change simply by taking a photo of it.
Introduction to the topic: Our new video «A quick guide to Quantum cryptography».
What motivates you personally to research quantum cryptography?
I studied Physics, so I was already fascinated by quantum physics as a student. It’s strange because many quantum phenomena contradict our everyday notions and you don’t experience them in normal life. I’ve always been attracted to these phenomena, although I wasn’t thinking specifically about quantum cryptography at the time. At the same time, I was already interested in cyber security during my studies. Now I can combine both interests.
Quantum physics, quantum computers and quantum cryptography
Quantum physics has had an enormous impact on our lives in recent decades. We use quantum technologies everywhere, usually without realizing it. These technologies date back to what some call the «first quantum revolution»: the invention of two building blocks, the laser and the transistor. Without these two building blocks, there would be no computers. While quantum computing aims to use quantum physics to improve our computing capabilities, quantum cryptography aims to improve the way we perform certain cryptographic tasks such as secure communication, and in some cases even makes things possible that were previously considered impossible.
Quantum computers use the principles of quantum mechanics. They can solve certain mathematical problems very efficiently. This capability gives them the potential to break the security of many cryptographic algorithms. That is why many applications and systems are currently switching to new quantum-safe algorithms—to so-called post-quantum cryptography. Some scientists believe that quantum computers have the potential to revolutionize many fields including materials science, pharmaceutical research, artificial intelligence, and optimization problems. They are currently still in the development stages.
Quantum cryptography uses the principles of quantum physics to create, among other things, information-theoretically secure communication channels. A well-known example is the quantum key distribution (QKD) protocol. This enables two parties to agree on a secret key. This means that attempts to eavesdrop on the communication with the goal of learning this secret can be detected. This allows for a level of security that cannot be attained with classical methods. Furthermore, quantum cryptography can also generate true random numbers, which might give rise to new protocols that were previously unthinkable.
What are you and the Applied Cyber Security Research Lab currently researching?
There is still a big gap between theory and practice in quantum cryptography. We are trying to narrow this gap so that quantum cryptography can be used outside academia and small proofs of concept. We are also investigating how these new devices can be integrated into existing IT systems to facilitate more widespread adoption. Of course, the ultimate goal is to have robust systems that can withstand future attacks by quantum computers. We pay particular attention to the fact that even small deviations in the implementation of quantum cryptography can jeopardize security and be exploited by attackers.
That sounds like a challenge.
It is! To avoid such problems, these devices need to be tested and standardized. We are trying to collaborate closely with companies to analyze, integrate and test their quantum cryptography products. For example, we are interested in determining whether or not these devices follow the theoretical security proofs. Finally, we investigate how deviations affect security and whether companies can reliably use these technologies in practice.
Why is it important to research quantum cryptography?
The obvious answer is that quantum cryptography enables information-theoretically secure communication. Many traditional encryption methods (for example RSA encryption) are only secure as long as certain mathematical problems remain inefficient to solve. Or as long as more advanced technologies such as quantum computers are not available on the market. Quantum cryptography, on the other hand, is based on physical laws, demonstrably secure and capable of protecting us from attackers now and in the future.
Quantum cryptography might enable technological inventions that we cannot even imagine today.
And the less obvious answer?
Quantum cryptography enables a completely new type of secure communication and has led to significant theoretical advances in information theory, which could be applied to other areas. It might eventually enable technological inventions that we cannot even imagine today.
Can you give us an example?
We won’t know what else technology will bring until we push forward and do whatever basic scientific research deems possible. I’m sure Einstein wasn’t thinking of a barcode reader, a DVD player or a gravitational wave detector when he laid the theoretical foundations for laser technology at the beginning of the last century.
What exactly can quantum cryptography already do today?
Quantum cryptography enables the creation of secure keys over insecure connections. These keys are used to encrypt data transmissions and ensure only people who are authorized can read the information. Any attempt to eavesdrop on the communication would change the quantum states and thus be detected immediately.

A quantum random number generator generates absolutely random numbers using the principles of quantum mechanics. This true randomness makes it an indispensable tool for cryptography and data security.
In addition, quantum cryptography is already used today to generate high quality random numbers, which are crucial for many cryptographic applications. All our devices use huge amounts of randomness and could not function properly without them (for example, to connect to WiFi networks, to visit websites, to receive updates…). As for QKD, this is not widely used yet, meaning QKD networks are currently limited to experiments in universities, and small or medium proofs of concepts. But this could well change in just a few years.
Why is it important to generate truly random numbers?
Computers often only generate seemingly random numbers. If an attacker can learn something about how they were generated (for example, the exact time or some small seed), they might be able to crack those numbers. Genuinely random numbers are crucial for cryptography and very important for other tasks like simulations. That is why we are researching how to use and integrate quantum random number generators. We have a commercial device that generates quantum random numbers. But even these types of devices are not perfect and have to be characterized and their output postprocessed.

In the Quantumlab, the team integrates quantum cryptographic devices into existing IT infrastructure and develops and investigates secure use cases. For example, they use a quantum random number generator to encrypt files or to create a distributed randomness beacon.
Can you give us three examples of applications that are already commonly used today?
There are smartphones like the Samsung Quantum that already run with chips that generate random numbers using quantum cryptography. You can buy quantum random number generators for around CHF 1,000. Companies such as ID Quantique or Toshiba offer ready-to-use devices for quantum key distribution (QKD), but they are still quite expensive. There are also national projects in countries like China and South Korea, in which quantum cryptography is being tested. The EU is also planning a QKD network with satellites (Eagle-1 project). Many laboratories around the world are currently researching this technology
Quantum cryptography: not to be confused with post-quantum cryptography
You are also conducting parallel research into post-quantum cryptography. How is this related to quantum cryptography?
While quantum cryptography is based on the principles of quantum physics, post-quantum cryptography has nothing to do with quantum physics—or not directly. The fact is that quantum computers might soon be able to crack conventional encryption methods such as RSA. That is why we need to migrate to cryptographic algorithms that are secure against attacks by quantum computers. Many applications and systems are therefore currently switching to new quantum-safe algorithms.
What does this migration to post-quantum cryptography look like?
The migration is happening right now! For example, Google and Cloudflare have already changed to a quantum-safe key exchange algorithm when connecting to their servers. Other migrations are more difficult, such as migrating to quantum-safe digital signature, and it will take some more time. We will probably see the first Certificate Authorities (CA) offer quantum-safe certificates by the end of 2026. Although there are currently no quantum computers strong enough to break cryptographic systems, we need to prepare for when they will be. Standardization organizations in the US and Europe have already created roadmaps for migration.
Why is it important to start migrating to post-quantum cryptography now?
First, there is the «harvest now, decrypt later» scenario. This could involve attackers storing encrypted communications now and decrypting them later, when quantum computers have become available. Secondly, there is the problem of legal history: documents that are digitally signed today must remain valid for 30 or 50 years. If a quantum computer can break these signatures, someone could forge documents and that would be a big problem. Finally, migrations are never easy. Only when trying new things, one will encounter problems that were not anticipated. For example, the management of the new quantum-safe certificate could be challenging. We are currently conducting a research project with essendi it AG on this very topic.
How do you see the future of quantum-safe cryptography?
On the one hand, quantum cryptography promises the highest possible level of security, but requires quantum communication channels, either through direct fiber optic cables or direct ground-satellite connections. This is currently still difficult to implement in practice. Post-quantum cryptography, on the other hand, is software-based and can be easily deployed to replace traditional cryptography. In contrast to quantum cryptography, post-quantum cryptography can also be used on currently available hardware. I think we will see a huge adoption of post-quantum cryptography in the next five to ten years. For QKD we will have to wait a bit longer. What is important to emphasize is that the two solutions are complementary, so I can imagine a future where the internet backbone is protected using quantum cryptography, while connections to end users are protected with post-quantum cryptography.
Author: Yasmin Billeter
published on: 12 August 2024

Iyán Méndez Veiga
Expert in quantum cryptography
Is researching at the Lucerne School of Computer Science and Information Technology as a member of the Applied Cyber Security Research Lab. He holds a BSc in Physics from the University of Oviedo and a MSc in Quantum Information and Quantum Technologies from the University of Ulm in Germany. Since October 2021, he has been working on his PhD as an external student at the ETH Zurich with a research assignment at the HSLU’s School of Computer Science and Information Technology.
Application-oriented research, development and consulting: the Applied Cyber Security Research Lab is a research team at the Lucerne School of Computer Science and Information Technology. It conducts research into secure applications and data protection. They investigate how secure and powerful devices can be developed and integrated into existing IT systems.
News from our School on LinkedIn. ? Follow us now!


Kommentare
0 Kommentare
Danke für Ihren Kommentar, wir prüfen dies gerne.